
What is Data Loss Prevention (DLP)




A web application firewall is a specific form of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service. A WAF or web application firewall helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. WAF, or the Web Application Firewall, is an integral part necessary for any effective solution to security, providing enhanced security to websites and enhancing the general posture of security.
What is Web Application Firewall (WAF)?

Why we need Web Application Firewall for our organization?
Features of Web Application Firewall
Web traffic filtering
WAF Bot Control
Account takeover fraud prevention
Full feature API
Real-time visibility
Endpoint security is the process of protecting entry points of end-user computers including desktop, laptop, and mobile devices from being used by malicious attackers and campaigns. In general, an endpoint security software works by employing an agent-server model of communication. The agent application is installed on all the endpoints and it gather and pull data from time to time, some of which are unpatched vulnerabilities, missing patches, etc.
What isEnd Point Protection (AV/NGAV)?
Why we need End Point Protection for our organization?

Features of End Point Protection
Threat protection
Device and application control
Data loss protection
Intelligent alerting and reporting
Automated detection and remediation
Flexible deployment options
Application Control
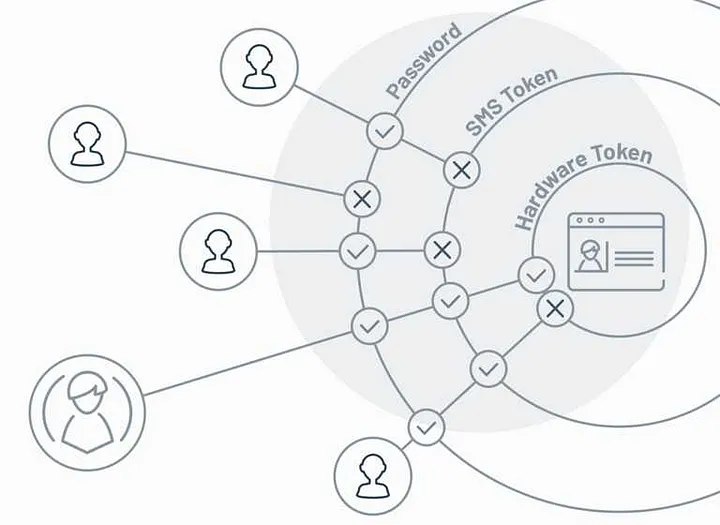
Email Verification – This is an email that a user receives with a link that verifies his account or a code. The user must either click on the link or type the verification code so that the he/she can be allowed to access the resources.What is Multi-Factor Authentication?
Why we need Multi-factor Authentication for our organization?

Features of Multi-factor Authentication
Easy to Implement
Adaptive
Role-Based Multi-Factor Authentication Tool
Cloud-Based Multi-Factor Authentication Software
Hard Tokens & Soft Tokens
Customizable
Multi Authentication Modes
Phone Verification – OTP(one time password) is sent to the phone number you used at the time of account sign-up and this is required when accessing the account.
Browser Push Notifications – One gets created on the browser, which helps in pulling the verification code and further aids in the confirmation of the user.
It can also be noted that Biometrics – Based MFA is most secured authentication method hard to break as discussed below. Biometric identification using finger prints, voice command or even scans that mimic the human retina can be used to identify the users.
What is Firewall/UTM/NGFW?

Why we need firewall for our organization?
What is the importance of having a firewall for our organization?
Features of Unified Threat Management
Firewall
Link Load Balance
SD-WAN
Site to Site VPN
Client/Remote VPN
Gateway Antivirus
Web Content Filtering
Intrusion Prevention System
Application Control
Bandwidth Management
Sand Boxing
Antispam
Reporting